
Organizational security protects businesses from cyber threats through comprehensive policies, proven security models, and employee awareness. This guide covers essential security frameworks including Bell-LaPadula, Biba, Clarke-Wilson, and Zero Trust models, plus seven actionable strategies:
- regular audits
- employee training
- on-premise deployment
- access controls
- encryption
- data hygiene, and
- physical security.
Learn how to balance security with productivity using modern collaboration platforms that enforce policies transparently while enabling seamless teamwork across cloud, on-premise, or air-gapped environments.
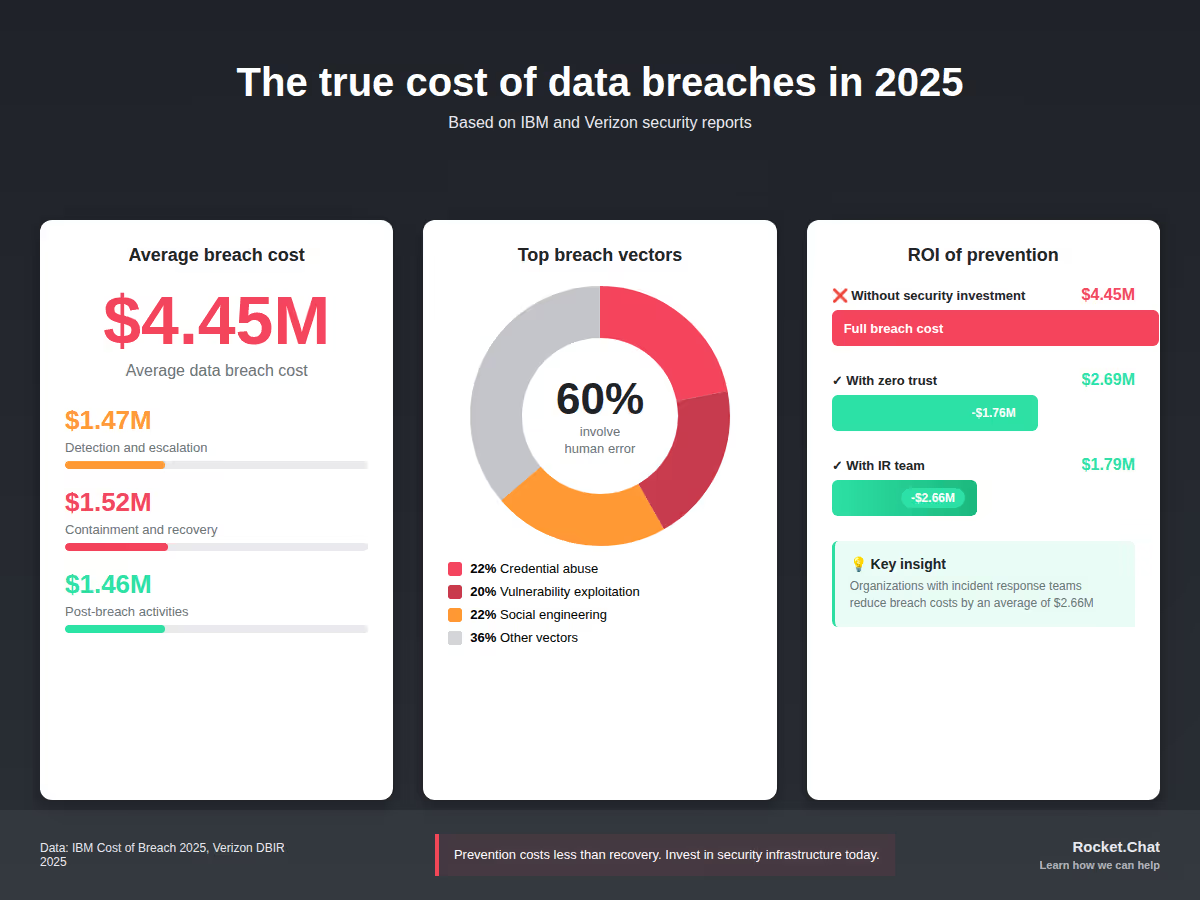
Modern organizations face unprecedented cybersecurity challenges. According to the 2025 Verizon Data Breach Investigations Report, credential abuse and vulnerability exploitation account for 42% of all confirmed data breaches, with the average breach costing $4.45 million to resolve based on IBM's 2025 Cost of a Data Breach Report.
Organizational security encompasses the policies, procedures, and technologies that protect your business from cyber threats. This guide explains practical security models, essential protocols, and proven strategies to safeguard your data while enabling productive collaboration.
What you'll learn:
- Core security models for data protection
- Essential security policies every organization needs
- Seven actionable ways to strengthen security posture
- How to balance security with team collaboration
Understanding organizational security policies
An organizational security policy is the foundation of your cybersecurity program. This document defines roles, responsibilities, security goals, and your approach to risk management.
According to Gartner research, 85% of CEOs now recognize cybersecurity as critical for business growth, not just a technical concern. Your security policy should address:
- Scope and objectives: Clear security goals aligned with business needs
- Roles and responsibilities: Who owns security at every level
- Compliance requirements: Industry regulations (HIPAA, GDPR, CCPA)
- Risk management approach: How you identify and mitigate threats
- Incident response procedures: Steps when breaches occur
Data security is essential for businesses that deal with sensitive information regularly. For organizations handling sensitive communications, implementing secure team chat solutions is essential to enforce these policies across daily operations.
Classic security models for data protection
Security models provide frameworks for maintaining confidentiality, integrity, and availability of your data. Here are the proven models organizations use:
Bell-LaPadula model: Protecting confidential data
The Bell-LaPadula model prevents unauthorized access to classified information through structured access controls. Developed in the 1970s, it remains relevant for government, defense, and highly regulated industries.

Three core rules:
- Simple security rule: Users read files at their security level or below
- Star security rule: Users write files at their security level or above
- Strong star security rule: Users read and write only at their exact security level
This model works best for government communication systems where information classification is critical.
Biba model: Maintaining data integrity
While Bell-LaPadula focuses on confidentiality, the Biba model prioritizes data integrity. It prevents lower-level users from corrupting higher-level data.

Three integrity rules:
- Simple integrity rule: Read files at same or higher security level
- Star integrity rule: Write files at same or lower security level
- Strong star integrity rule: Read and write only at same security level
Organizations using mission-critical communications benefit from Biba's focus on data accuracy and reliability.
Clarke-Wilson model: Commercial security framework
The Clarke-Wilson model addresses real-world business needs, focusing on preventing fraud and errors through:
- Transaction-based access: Users access data through defined programs
- Separation of duties: Multiple approvals for sensitive actions
- Audit logging: Complete transaction history for accountability

This model supports communication security in financial services, healthcare, and other regulated industries.
Zero Trust model: Modern security architecture
The Zero Trust model reflects today's distributed workforce reality. It assumes every access request is potentially malicious, regardless of origin.

IBM's 2025 Cost of a Data Breach Report found that organizations implementing Zero Trust reduced breach costs by an average of $1.76 million compared to those without it.
Five Zero Trust principles:
- Assume all users and devices are hostile until verified
- Threats exist both inside and outside the network
- Network location doesn't determine trust
- Authenticate and authorize every user, device, and data flow
- Use dynamic policies based on multiple data sources
Zero Trust architecture is essential for encrypted messaging platforms where endpoint security cannot be guaranteed.
Who owns organizational security?
Everyone.
The 2025 Verizon Data Breach Investigations Report reveals that 60% of breaches involve human error, misuse, or social engineering. Security is not just an IT responsibility but an organizational culture.
Key stakeholders include:
- Leadership: Sets security priorities and allocates resources
- IT/Security teams: Implement technical controls and monitor threats
- Employees: Follow security protocols in daily work
- Partners/Vendors: Maintain security standards in their systems
- Customers: Protect credentials and report suspicious activity
Organizations with mature security culture experience 40% fewer employee-driven incidents, according to Gartner's 2025 cybersecurity trends report.
When evaluating collaboration tools, consider whether the platform supports your security culture.
Learn more about selecting the most secure messaging apps that enable policy enforcement.
Seven practical ways to strengthen organizational security
1. Conduct regular security audits and testing
Continuous assessment identifies vulnerabilities before attackers exploit them. The 2025 Verizon Data Breach Investigations Report found that organizations fully remediating edge device vulnerabilities within 32 days avoided 20% of potential breaches.
Audit priorities:
- Third-party integrations and vendor access
- User permission levels and access controls
- Security patch status on all systems
- Compliance with industry regulations
For government agencies, security audits must extend to all communication platforms used for official communications, including evaluation of government messaging apps for security compliance.
2. Invest in continuous employee training
Human error remains the top breach vector. Verizon's 2025 report shows that 22% of breaches involved social engineering, with phishing as the primary method.
Effective training includes:
- Monthly security awareness updates
- Simulated phishing exercises
- Role-specific security protocols
- Incident reporting procedures
- Password management best practices
Training should cover how to use chat platforms securely, including recognizing impersonation attempts and suspicious links.
3. Deploy on-premise solutions for sensitive data
Cloud services offer convenience, but highly regulated industries benefit from on-premise deployment's control and compliance advantages.
On-premise benefits:
- Complete data sovereignty
- Customizable security controls
- Regulatory compliance (HIPAA, FedRAMP)
- Protection from cloud service outages
- No third-party data access
For organizations requiring maximum isolation, air-gapped collaboration provides defense in depth by physically isolating critical systems from external networks.
4. Implement granular access controls
The principle of least privilege limits damage from compromised credentials. Verizon's 2025 report found that 53% of breaches involved stolen credentials.
Access control best practices:
- Role-based access control (RBAC)
- Multi-factor authentication (MFA) on all accounts
- Regular access reviews and deprovisioning
- Privileged access management (PAM) for administrators
- Just-in-time access for sensitive operations
Document management systems must integrate with your access controls to ensure only authorized users view sensitive files.
5. Deploy end-to-end encryption
Encryption protects data both in transit and at rest. Even if attackers intercept communications, encrypted data remains unreadable without decryption keys.
Encryption requirements:
- End-to-end encryption for messaging
- TLS 1.3 for data in transit
- AES-256 for data at rest
- Encrypted backup storage
- Key management protocols
Organizations handling sensitive communications should prioritize solutions that provide encryption by default and meet communication security standards for their industry.
6. Maintain rigorous data hygiene
Poor data quality creates security vulnerabilities and operational inefficiencies. Clean, organized data is easier to protect and monitor for anomalies.
Data hygiene practices:
- Regular data classification reviews
- Automated data validation
- Duplicate record elimination
- Secure data disposal procedures
- Data retention policy enforcement
7. Secure physical infrastructure
Physical security prevents unauthorized hardware access, theft, and environmental damage. IBM's 2025 report found that physical breaches, while less common, cost an average of $3.8 million to resolve.
Physical security measures:
- Biometric access controls
- Video surveillance systems
- Environmental monitoring (temperature, humidity, fire)
- Secure equipment disposal
- Disaster recovery site protection
- Visitor access logging
Balancing security with collaboration
The tension between security and productivity is real.
Overly restrictive security slows business operations, while weak security exposes organizations to costly breaches.
Modern collaboration platforms solve this challenge by embedding security controls that work transparently. Teams can communicate freely while automated systems enforce policies, encrypt data, and log activity for compliance.
At Rocket.Chat, we design solutions that prioritize both security and usability. Our platform supports:
- Regulatory compliance: HIPAA, GDPR, CCPA certified
- Flexible deployment: Cloud, on-premise, or air-gapped
- Open source transparency: Community-audited codebase
- Enterprise-grade encryption: End-to-end by default
- Granular access controls: Role-based permissions
Whether your organization needs secure collaboration for daily operations or specialized solutions for classified environments, the right platform makes security seamless. For mission-critical operations, explore how out-of-band communication channels provide additional security layers during emergencies.
Essential resources for secure business communication
Organizations serious about security need comprehensive evaluation criteria. Download our checklist: 12 Things to Look for in a Secure Business Communication Platform to assess your current tools against industry standards.
For government agencies with unique security requirements, learn more about specialized government chat solutions designed for public sector compliance and security standards.
Taking action on organizational security
Cybersecurity threats continue evolving, but the fundamentals remain constant: strong policies, employee awareness, defense in depth, and tools that enforce security without hindering productivity.
Start with these immediate steps:
- Audit your current security posture against the seven strategies above
- Identify gaps in your policy coverage and technical controls
- Schedule security awareness training for all employees
- Evaluate whether your communication tools meet security requirements
- Document incident response procedures and test them regularly
Organizations implementing comprehensive security programs see measurable benefits. According to IBM's 2025 research, companies with incident response teams and regular testing reduced breach costs by an average of $2.66 million compared to those without.
For organizations with critical operational requirements, consider how mission-critical communications platforms ensure availability and security during high-stakes situations.
Contact our security team to discuss how Rocket.Chat can support your organizational security goals.
Frequently asked questions
What is the difference between organizational security and cybersecurity?
Organizational security is the broader concept encompassing all security measures, including physical security, personnel security, and information security. Cybersecurity specifically focuses on protecting digital assets, networks, and data from cyber threats. Both are essential components of a comprehensive security program.
How often should security policies be updated?
Review and update security policies at least annually, or immediately when: major technology changes occur, new regulations take effect, significant breaches impact your industry, or your organization's risk profile changes. Quarterly reviews help ensure policies remain effective against evolving threats.
What security model is best for small businesses?
Small businesses benefit most from practical, scalable approaches like Zero Trust principles combined with fundamental security hygiene: employee training, MFA, regular backups, and patch management. Rather than complex academic models, focus on the seven practical strategies outlined above and select collaboration tools with built-in security features.
How much should organizations budget for security?
Gartner forecasts global information security spending will reach $212 billion in 2025, representing a 15% increase year-over-year. For individual organizations, security budgets typically range from 4-13% of overall IT spending, depending on industry, regulatory requirements, and risk tolerance. The cost of prevention is always lower than the average $4.45 million cost of a data breach.
Can encrypted messaging be both secure and compliant?
Yes. Modern encrypted messaging platforms designed for enterprises support both security and compliance requirements. Look for solutions offering encryption, audit logging, data retention policies, e-discovery capabilities, and certifications for regulations applicable to your industry (HIPAA, GDPR, etc.). The right platform provides security without sacrificing compliance or usability.
Frequently asked questions about <anything>
organizational security
What is the difference between organizational security and cybersecurity?
How often should security policies be updated?
What security model is best for small businesses?
How much should organizations budget for security?
Can encrypted messaging be both secure and compliant?


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment



.avif)


